
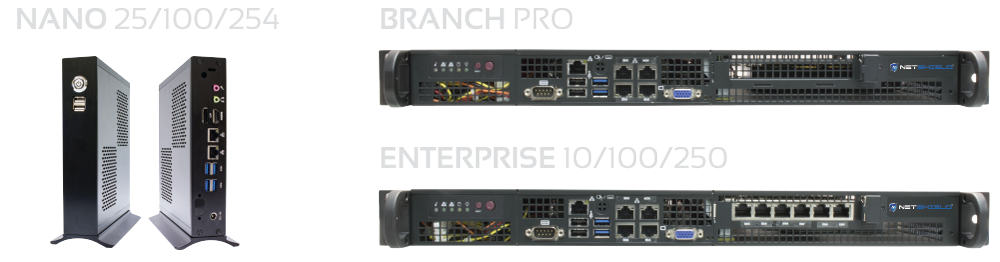
Plug Anywhere, Discover Everywhere
Agentless Access
Control
Detect, Alert, Block and
Isolate
PHYSICAL
MOBILE
VIRTUAL
IOT
Agentless Security
Malware, Ransomware & Phishing Attack Prevention
Detect and Block Rogue Assets
Hardware & Software Agnostic
Vulnerability Assessment
Dynamic VLAN Assignment & Quarantining
Non-inline, Plug Anywhere. Discover Everywhere
Blocks rogue and compromised assets in real-time
Helps address GDPR framework to maintain compliance
Smart switch integration to isolate rogue assets

First to deliver cyber security hardware with built-in cyber insurance
Cyber Insurance - Coverage up to $250,000 included
Currently available in the U.S.
Gain control of your network, identify all assets and block those who don't belong
Defense against zero day malware, ransomware and phishing attacks
Agentlessly audit assets, identify Common Vulnerabilities and Exposures (CVE)
KEY FEATURES
Assets detection & instantaneous blocking
- Plug anywhere, discover everywhere
- Discover All Physical, Virtual, Mobile,
IoT assets
Malware/Phishing Detection and Prevention
- Monitor egress traffic to discover connection attempts to known malicious servers
- Employ instantaneous blocking
Auditing & Vulnerability Assessment
- Identify Common Vulnerabilities and
Exposures (CVEs)
Agentless
- Easy to Diploy – No need to load agents on end points
- Simple to configure
Non-Inline
- No performance impact
- Connects the same way as a PC would
Plays Well With others
- Layered network approach
- Hardware and software agnostic
- Smart switch integration to isolate rogue assets
- Third party integrations

STATE-OF-THE-ART ARTIFICIAL INTELLIGENCE
+
AGENTLESS NETWORK ACCESS CONTROL
NETSHIELD
- Network Access Control
- Detect rogue and new network devices
- Prevent unknown/untrusted devices from connecting to the network
- Highly scalable, affortable and simple to manage, network security solution
- No need to deploy agents
CYGLASS
- Network Behavior Anomaly Detection
- Artificial Intelligence & Machine Learning analyzes and prioritize tremendous amounts of network data to find abnormal network behavior
- Affordable SaaS model
- Detect Command & Control events on known assets

